Cryptography ICE Cube experiment
A compact experiment aimed at enhancing cybersecurity for future space missions is operational in Europe’s Columbus module of the International Space Station, running in part on a Raspberry Pi Zero computer costing just a few euros.
“Our CryptIC experiment is testing technological solutions to make encryption-based secure communication feasible for even the smallest of space missions,” explains ESA software product assurance engineer Emmanuel Lesser. “This is commonplace on Earth, using for example symmetric encryption where both sides of the communication link share the same encryption key.
“In orbit the problem has been that space radiation effects can compromise the key within computer memory causing ‘bit-flips’. This disrupts the communication, as the key on ground and the one in space no longer match. Up to now this had been a problem that requires dedicated – and expensive – rad-hardened devices to overcome.”
Satellites in Earth orbit might be physically remote, but still potentially vulnerable to hacking. Up until recently most satellite signals went unencrypted, and this remains true for many of the smallest, cheapest mission types, such as miniature CubeSats
But as services delivered by satellites of all sizes form an increasing element of everyday life, interest in assured satellite cybersecurity is growing, and a focus of ESA’s new Technology Strategy for this November’s Space19+ Ministerial Council.
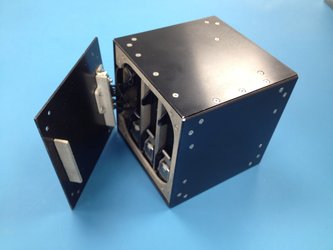
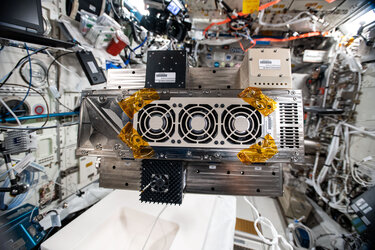
CryptIC, or Cryptography ICE Cube, - the beige box towards the top of the image, has been a low-cost development, developed in-house by ESA’s Software Product Assurance section and flown on the ISS as part of the International Commercial Experiments service – ICE Cubes for short. ICE Cubes offer fast, simple and affordable access for research and technology experiments in microgravity using compact cubes. CryptIC measures just 10x10x10 cm.
“A major part of the experiment relies on a standard Raspberry Pi Zero computer,” adds Emmanuel. “This cheap hardware is more or less flying exactly as we bought it; the only difference is it has had to be covered with a plastic ‘conformal’ coating, to fulfil standard ISS safety requirements.”
The orbital experiment is operated simply via a laptop at ESA’s ESTEC technical centre in the Netherlands, routed via the ICE Cubes operator, Space Applications Services in Brussels.
“We’re testing two related approaches to the encryption problem for non rad-hardened systems,” explains ESA Young Graduate Trainee Lukas Armborst. “The first is a method of re-exchanging the encryption key if it gets corrupted. This needs to be done in a secure and reliable way, to restore the secure link very quickly. This relies on a secondary fall-back base key, which is wired into the hardware so it cannot be compromised. However, this hardware solution can only be done for a limited number of keys, reducing flexibility.
“The second is an experimental hardware reconfiguration approach which can recover rapidly if the encryption key is compromised by radiation-triggered memory ‘bit flips’. A number of microprocessor cores are inside CryptIC as customisable, field-programmable gate arrays (FPGAs), rather than fixed computer chips. These cores are redundant copies of the same functionality. Accordingly, if one core fails then another can step in, while the faulty core reloads its configuration, thereby repairing itself.”
In addition the payload carries a compact ‘floating gate’ dosimeter to measure radiation levels co-developed by CERN, the European Organisation for Nuclear Research, as part of a broader cooperation agreement
And as a guest payload, a number of computer flash memories are being evaluated for their orbital performance, a follow-on version of ESA’s ‘Chimera’ experiment which flew on last year’s GomX-4B CubeSat.
The experiment had its ISS-mandated electromagnetic compatibility testing carried out in ESTEC’s EMC Laboratory.
“CryptIC has now completed commissioning and is already returning radiation data, being shared with our CERN colleagues,” adds Emmanuel. “Our encryption testing is set to begin in a few weeks, once we’ve automated the operating process, and is expected to run continuously for at least a year.”