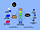
Figure 1. The Data Dissemination Network (DDN) via which ESRIN's services are made available on-line to users around the world

ESRIN provides a large number of online services to users all over the world via a complex telecommunications network. As the number of services offered grows and their geographical coverage expands, the network becomes increasingly vulnerable to a security threat.
ESRIN has therefore developed a security policy to protect all of the resources connected by the network. Operational roles and responsibilities for security have been established, and measures to heighten awareness of an installation's security exposure have been implemented. In addition, the ESRIN networks have been reorganised based on an assessment of each host computer's required security level. Further measures, such as authentication and access control measures, will be phased in as deemed necessary.
Access to application services on a computer system is normally controlled by the system using traditional operating-system protection measures. Those measures are in accordance with predefined policies that vary from maximum openness to strictly controlled identity- and role-based access.
The introduction of computer networks adds a new dimension to the problem of securing access to computer services. The security of worldwide interconnected networks becomes increasingly important as a service's geographical coverage grows and it becomes more exposed to 'attacks' by 'hackers' who, safely sitting in their offices or homes anywhere in the world, can wander through 'cyberspace', bypassing all barriers and posing a serious threat to the integrity and privacy of computer systems and the networks. Network operators will face a great fight in the years to come as they attempt to secure their networks. Unfortunately, the efforts of those responsible for fighting against 'trespassers of the computer frontier' are not always duly acknowledged by the general public. The victims of computer crime try to avoid any publicity as well as the embarrassment and negative effect of being known as the subject of an attack, thus revealing the vulnerability of their installations. This makes computer crimes harder to fight since it involves fighting an unknown enemy. In addition, a romantic halo surrounds the hackers: they appear to be freedom fighters. A few recent books describing some real incidents, however, have tried to shed light on the computer hacking 'underculture', revealing the true, more prosaic side of what is now considered to be a criminal activity.
ESRIN, the ESA establishment located in Frascati, Italy, is particularly concerned about network security. ESRIN is responsible for the provision of user services associated with data and products from many Earth observation and astronomy satellites, with bibliographic information on space and space-related domains and with information systems in support of ESA activities. To do so, ESRIN operates a complex telecommunications network that connects the establishment with a large number of ground facilities and user entities distributed all over the world, offering on-line access to .a number of services. ESRIN is also responsible for the European nodes connected to international Earth observation and scientific networks.
By definition, these services are open to any users in the world. Therefore, the problems of network and system security, not only for the ESRIN facilities but also for the other entities linked to it through the network, are of prime concern.
ESRIN has therefore established a consistent security policy to protect all the resources connected by the network, in keeping with the general principles on protection of information assets defined by ESA. The focus is on network security since the network is considered to be the medium through which attacks on the resources and services offered by ESRIN may originate, and is thus the most appropriate place to 'build fences'. The policy is outlined here.
A plan for the implementation of the security policy has also been developed and some aspects are now being implemented. Increasingly sophisticated security measures will be phased in as deemed necessary based on the assessed risk to which the establishment is exposed. Such an 'evolution path' includes the protection of individual pieces of information with the establishment of a number of security levels and the classification of resources and host computers with respect to them. This evolution will occur in accordance with the general guidelines laid down by ESA's Risk Management Office through its Data Security Programme.
such as electronic mail, directory, file transfer, bulletin boards, newsletters, conferences and gateway facilities for mail and file transfer.
Users of ESRIN services are mainly interested in the following domains:
The user communities are widely spread out and are located around the world. They include users with very different hardware and software capabilities, and with varying levels of knowledge, ranging from those who are very familiar with computingandnetworkingto those who do not have any modern tools available at their site. Therefore, ESRIN is bound to offer a widely ranging and flexible support.
In general, ESRIN's tasks include the management of the facilities to acquire, process, archive and distribute satellite data and other space-related information, and the provision of comprehensive data retrieval and dissemination systems with specialised functions to support operations on catalogues, directories and inventories, correlation of data, and simultaneous and coordinated access to different remote archives. Electronic mail services are also offered.
The infrastructure of hosts and networks at ESRIN has grown rapidly in the last decade, in parallel with ESRIN's increasing responsibility to support user interface and data handling tasks. In particular, the development of the ground segment for ESA's ERS-1 Earth observation satellite has meant at least a ten-fold increase in the complexity and scope of the ESRIN responsibility. Moreover, in order to prepare for the upcoming, even more complex Earth-observation missions like Envisat, ESRIN started last year to revise and redesign much of its telecommunication infrastructure.
Since its telecommunication links must be worldwide, ESRIN is actively working with the European Union on the establishment of a European network for the exchange of environmental data, as well as with the international Committee for Earth Observation Satellites (CEOS) on the interconnectivity and interoperability of networks, databases, directories, inventories and catalogues among the agencies and entities associated with Earth-observation satellite data.
ESRIN's services are made available on-line to users around the world via the Data Dissemination Network (DDN), by means of the ESRIN telecommunication infrastructure (Fig. 1). In particular, the DDN provides the 'highway'for the transport of two types of data traffic:
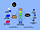
Figure 1. The Data Dissemination Network (DDN) via which ESRIN's services are made available on-line to users around the world
The DDN traffic is related to:
The DDN includes a Local Area component, which covers the whole ESRIN site and provides connectivity to all hosts and terminals on site, and a Wide Area component, made up of 'access points'located in ESA Member States and interconnected by international research networks such as Internet and SPAN.
An access point is a host computer with a well-known address to which users in one country can connect. It links all relevant local institutes and concentrates the traffic of all national users. Remote users accessing ESRIN services via the DDN remote access points or via the Internet are presented with a menu listing all the available services and requesting the user's choice.
The requirement to provide 'open'access to an external user (i.e. a non-ESRIN user) on a host computer supporting one or more user services through a network, may seem to contradict the need for basic measures to control the access to the information resources. In fact, a totally uncontrolled access could create problems not only to local systems but also to the systems 'downstream'on the network that the local host provides further access to. This issue is of particular concern for the Earth-observation systems, where a user is supposed to be able to access the system without restrictions and with as user-friendly an interface as possible.
Up to now, the networks have not imposed any restrictions on the accessibility of the services, that is, no security checks have been performed at the network level. Instead, the 'user validation'has been performed directly at the application level by the hosts supporting the services, under their responsibility. This is achieved by restricting the service to 'registered'users, for example, by requesting user identification and the proper password at the time of log-in. The service of on-line jumping to other remote hosts requires special security measures and should be limited to identified users. In some other cases, hosts do not perform any check on a user's eligibility for services and make services available to 'anonymous' users. This is the case with services available via World Wide Web (WWW) (e.g. X-mosaic), Gopher, or Z39.50 (WAIS).
The classification of hosts and services currently in operation at ESRIN with respect to the category of the accessible services and related restrictions is given in Table 1.
Additional security measures at the network level, beyond those at the application level just described, must be introduced to provide adequate security.
A distinction should be made between a) the network connecting the host computers to one another, and b) the resources present on such host computers and made available to remote users through the network itself.
The network provides the basic connectivity among access points, to which the host computers are attached. The network is composed of hardware components and logical pieces that provide the routing among them from one source to a destination access point.
There are three different kinds of access to a service through the network:
Such accesses are traditionally mediated through security measures that check each user's identity against a registry in which the identity of those users who are authorised to access a computer, a service, or an individual resource are stored, usually associated with additional information (e.g. passwords) used to authenticate the users (level R, registered users). When the user has been identified, all the user's actions can be traced and accounted for.
However, userswho arenotregisteredor known can gain access to systems and services (level A, anonymous users). For example, non-registered users (behind which anybody, even a hacker, may be hiding) can connect to a service anonymously when accessisopen to all (e.g. an anonymous FTP), or by means of particular, well-known user names related to the service being offered (e.g. WWW or GDS).
Access by unknown users is not necessarily harmful if their activities can be limited to a previously defined, well-known subset of all possible system commands (this limited functionality is often characterised as a 'captive account'). Malicious intruders, however, can exploit the weaknesses of the operating system and gain access to the basic system from confined applications, thus proceeding into uncontrolled environments where they could possibly cause harm.
In other cases, unknown users can gain access to a system by guessing the names and passwords of legitimately registered users. This can be achieved when the passwords selected by the legitimate users are weak, being either obvious or well-known. This is particularly harmful because, once they are logged on, the intruder is disguised by the identity of an innocent user, so any harm they create will be attributed to somebody else.
Therefore, appropriate security measures are required even if the official policy for information management is to provide the utmost openness. Security measures, in fact, do not necessarily mean closing the doorsof a system, but carefully checking who gets in and for what purpose.
ESAIRS Information Retrieval Service EMITS Electronic Mail Invitation to Tender System (VT100 and TTY) EMITSWIN Electronic Mail Invitation to Tender System (Windows) GDS ESA Earth Observation Guide and Directory Service DODIS Official Document Distribution Service (VT100 and TTY) DODISWIN Official Document Distribution Service (Windows) CUIS Columbus Utilisation Information System(VT100) CUISWIN Columbus Utilisation Information System (Windows, Macintosh) ESALEX ESA Legal Text Service (VT100 and TTY) EECF Ers-1 European Central Facility ERSUS Ers-1 User Services VAS OSI Value Added Services QUIT Exit
Organisational measures
The first step when dealing with security is to establish the responsibilities of those em-powered to deal with security matters.
At ESRIN, the Information Security Office (ISO), the technical focal point for all network, computer and information security-related matters, monitors the security of the network and computer installations and issues instructions to counter risks and exposures. With the ISO'ssupport, the ESRIN management coordinates the application of the policies and guarantees their uniform enforcement throughout the establishment. In turn, an officer from each division is appointed to a Security Advisory Board that ensures the necessary consensus for all security measures. The security officers guarantee the application of the measures in each division.
Awareness measures
The security of the system must be constantly monitored, and a general awareness of security issues and threats maintained. Only when the real risks are known and quantified in terms of economic loss, can an effort (in terms of manpower and procurement of monitoring and enforcement tools) be justified to management.
Each system manager regularly follows a routine security 'checklist'to ensure that the appropriate levels of checks against the known vulnerabilities are in place. The items to be checked include the choice of passwords, the levels of file protection, and the boundaries of free-access captive accounts. The ISO regularly distributes advisory notes from the international security community, in particular from the Computer Emergency Response Team (CERT) (at Carnegie-Mellon University, USA), to increase the system managers'awareness and help in coping with newly discovered weaknesses. Modern legislation is also increasingly aware of computer security and the lack thereof, and now offers instruments for action, including at the legal level if necessary.
In order to assess the risks and the seriousness of an attack, system managers routinely monitor access by both external and internal users to the systems under their responsibility, and report any incidents or suspected incidents to the ISO. This also applies to the managers of the network itself, since network resources like modems, routers, management stations, and the access lines, as well as information like the routing tables and the network-level accesscontrol lists, are at the core of the security of the whole site.
Protection measures
Since the network is the most likely medium through which intruders can penetrate a system, the network is an appropriate place to enact basic security measures.
Protection measures at the network level have already been implemented at ESRIN. They include:
At the network level, however, only the addresses of calling parties are visible, so any measure enforced at that level can be applied to addresses only, and is transparent to the identities in application and human terms of the called and calling parties, as well as to the application semantics. In other words, protection at the network level cannot be a substitute for application-level protection, which must be addressed separately.
Protection measures at the application level include:
The first two measures have already been implemented at ESRIN. For the last two, the authentication and authorisation enhancement measures, the level of sophistication that will actually be implemented will be a direct function of the assessment of the risks.
As stated before, the network is the primary point of access where basic security measures can be enacted. Enactment of network-level protection measures is the first step to achieving adequate, overall security for any installation. To this end, the network structure at ESRIN has been reorganised according to two main criteria, accessibility and operativity, as follows:
A logical 'firewall'has been installed to prevent external accessors from reaching particular networks (and host computers) within the establishment (Fig. 3). The existence of a firewall at the network level does not imply that whatever is on the 'outside'of the wall is abandoned to the incursions of hackers: appropriate security measures at the application level protect those host computers and their information.
Four categories of networks have therefore been created (Fig. 4). Depending on the nature of theactivity performedon each host computer at ESRIN, that host computer is being assigned to one (and only one) of the network categories. To perform the transition, two procedures are used, one makes a computer accessible and the other makes a computer operational. The procedures include a number of tests and some formal constraints

Figure 3. A logical 'firewall'separates ESRIN's systems and services that do not have to be accessible to the external world from those that must be accessible

Figure 4. Four categories of network have been created. All host computers offering an operational service, whether they are accessible or non-accessible, are connected to different networks than those used for development or office support (non-operational)
The elements of ESRIN's newsecurity policy are summarised in Table 2.
The key to success in rendering secure a complex establishment like ESRIN from the information services point of view is to make the staff aware of the risks involved and of their personal responsibility in complying with the relevant security regulations in their daily activities, as stated by ESA's policy on the protection of computer operations. This has to happen with managerial support and with the staff's full consensus, without limiting their personal freedom with respect to professional activities and contact with the external world. One of the Information Security Office's tasks is therefore to run an awareness campaign targeted at the individual users, and aimed at garnering the maximum level of compliance with the defined rules.
The input and advice received from J. Bequignon, A. Bodini, P. Donzelli, M.E. Forcada, E. Onorato and R. Turco, are gratefully acknowledged.



 ESA Bulletin Nr. 80.
ESA Bulletin Nr. 80.